Lesson 6: Computer Networking
Computer Networking
A computer network is a group of computers connected to share resources, exchange files or talk to each other.
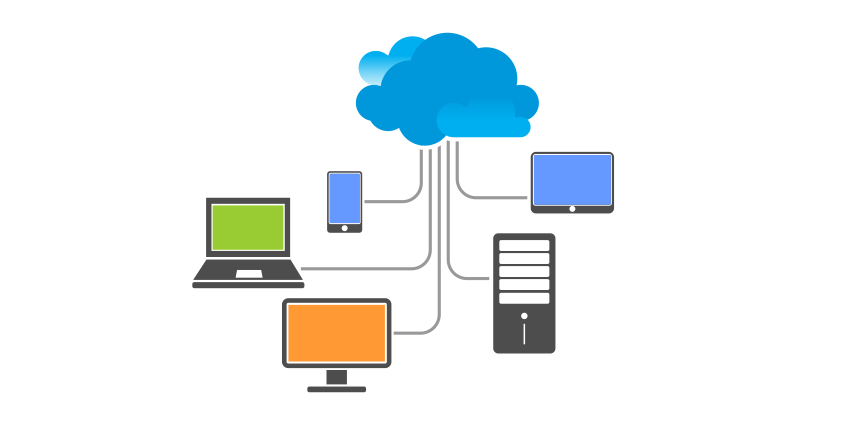
Several nodes (computers, printers, servers, storage devices, and so on) can be connected over a network using devices such as hubs, switches and routers.
There are mainly two types of network:
Local Area Network (LAN) is a computer network that connect two or more computer within local domains such as estates, colleges, hospitals, corporations, and so on.
Wide Area Network (WAN) is a computer network that is used for connecting computers that span a wide geographical area. The largest WAN is the internet.
Network use communication protocols based on which devices can talk to each other. Windows and Linux use TCP/IP.
OSI network model
Open System Interconnection (OSI) is the most widely used standard model. It is specified by ISO and describes the seven layers that computers use to communicate over a network.
The OSI model comprises the following layers:
Layer 1
The physical layer is used to transmit raw bit stream over physical media such as UTP cables/optics.
Layer 2
The data link layer is used to move frames from one node to another and it is responsible for the checksums that ensure that data does not have errors. Switches work on layer 2.
What is a switch? A switch is a network device that connects devices on a computer network by using packet switching to receive and forward data to the destination device.
Switches help to connect devices such as computers, printers, laptops, servers together to share resources in a small network.
IP addresses
Layer 3
The network layer is responsible for delivering packets from source to destination nodes. It uses IP addresses to identify nodes and uses routing protocols to route packets over different networks using routers.
An IP address is a numerical address assigned to each device in a network that uses internet protocol (IP) for communication.
For example, as your home needs a mailing address to receive packages, devices connected on a network need an IP address to receive messages.
So, when Computer A needs to talk to Computer B, computer A sends a message to the IP address of computer B, and also includes its own IP address, so that computer B can reply.

There are two versions of the IP addressing scheme: IPv4 and IPv6.
IPv4 is a 32-bit addressing protocol. Each address is split into four different sections and those numbers can range from 0 to 255.
Each section comprises of 8 bits, where there are only two possibilities 0 or 1.
So total values will be 2*2*2*2*2*2*2\*2=2^8[0-255]
IP addresses have four sections, separated by dots[0-255].[0-255].[0-255].[0-255]
So, in total, IPv4 can have up to 2^32 =4,294,967,2964 maximum possible addresses. But in the real world, there are more than 4 billion devices connected to internet, so we need another way to get more unique IP addresses.
There is a solution!
IPv6 is a 128-bit addressing protocol. It has sufficient addresses to cover all possible devices connected to internet.
An IPv6 address is split into 8 sections and each section has 4 hexadecimal numbers. The sections are separated by colon characters.
Hexadecimal number range from 0 to F, where A=10, B=11…..F=15.
Example of an IPv6 address:
2001:00bd:0042:0000:8c20:0000:07b0:7554
Each section comprises of 16 bits, each with a possible value of 0 or 1. The total number of bits in an IPv6 address is 16\*8=128
So, in total we can have 2^128 possible IPv6 addresses, which is 340 undecillion addresses. That’s a quite lot!!
Let’s talk about how IP works on Layer 3.
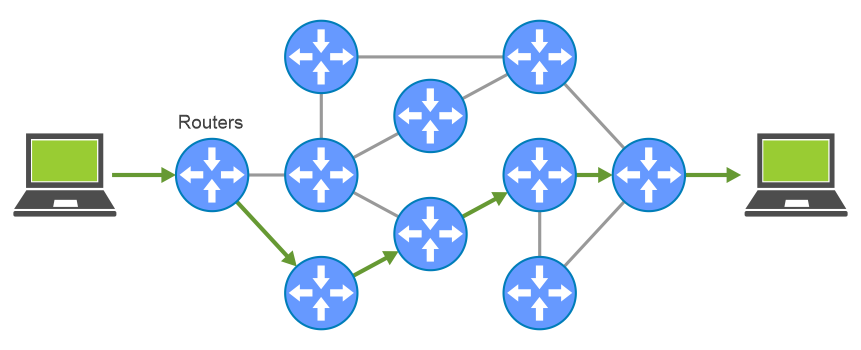
When using Internet Protocol (IP), a computer splits messages into packets and those packets hop from router to router to reach their destination.
A router is a device that forwards data packets between computer networks.
So why do we use routing?
If you are in Dublin and you want to send an image to your friend in London. What do you think will happen and how will this image be transferred from your phone to your friend’s phone in some other location?
Firstly, the image might be made up of tens of billions of bits, 1s and 0s. This is too many to send in one packet. So, the computer breaks the image into thousands of smaller packets.
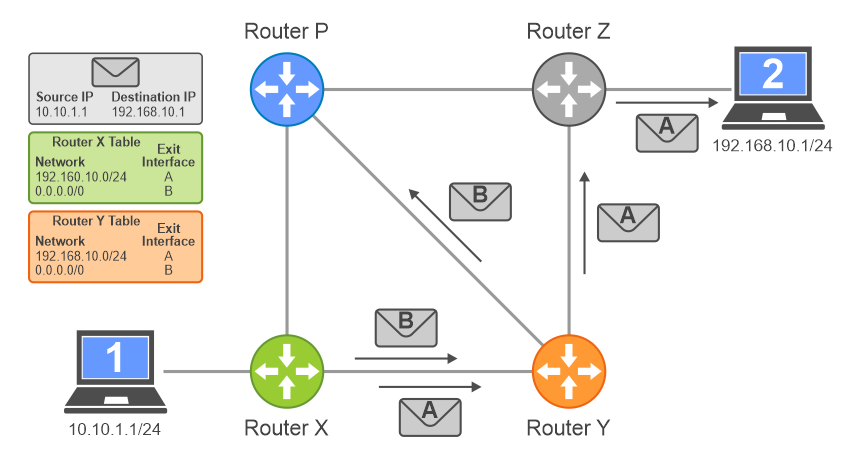
Each packet has the IP address of the source and the destination. Devices, such as routers, act as traffic managers to keep track of packets moving smoothly through the network.
Routers have routing tables where they keep record of exit interfaces to be used when a packet arrives, based on the destination address of the packet.
The gif below demonstrate how the data packets are transferred across the internet using the example of an email that consists of text, an image and a video. The data/information to be transferred is broken down into smaller data packets (in this gif, represented by the icons of an image, a video and a letter) and those travel through the network separately. When reaching the final destination, the email is then put back together.
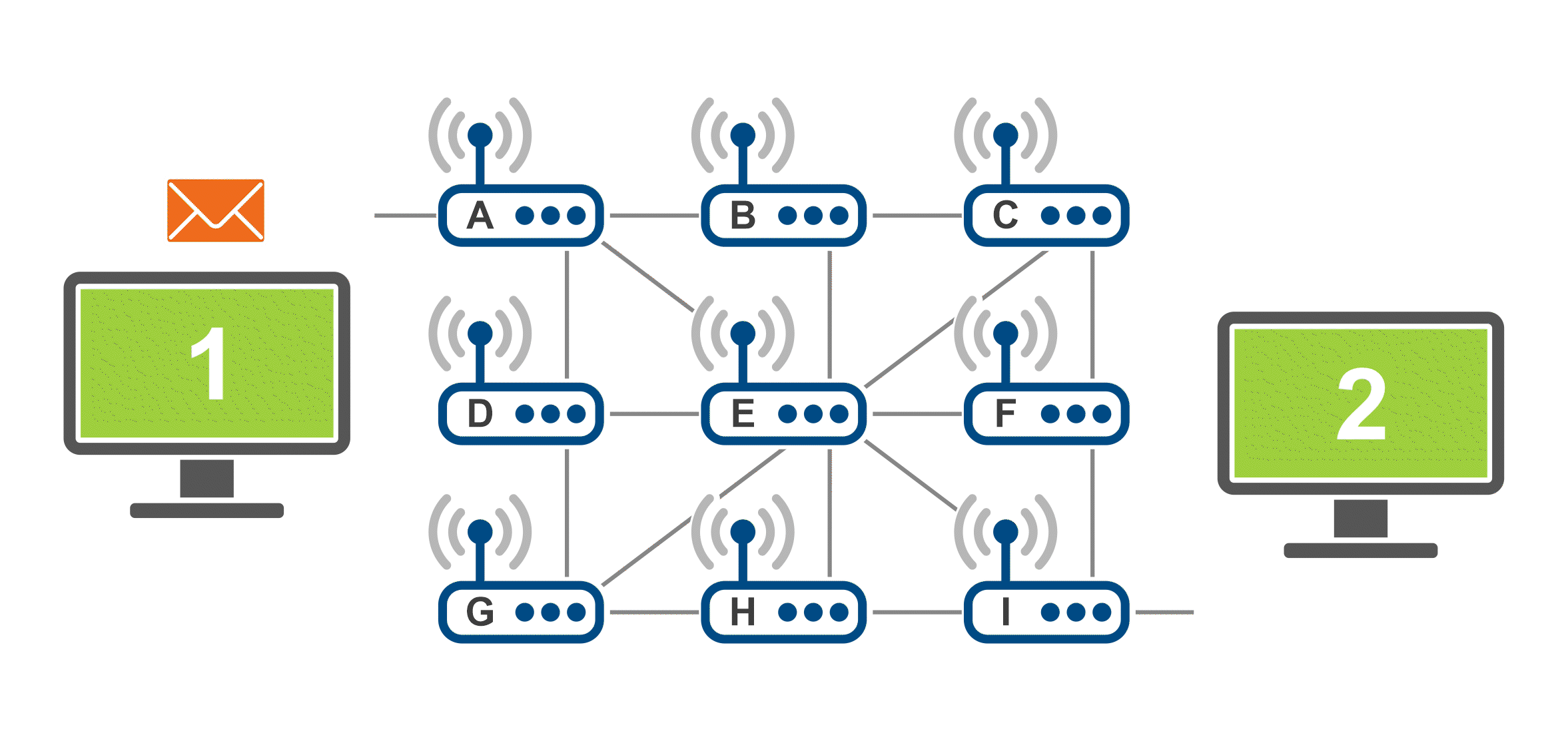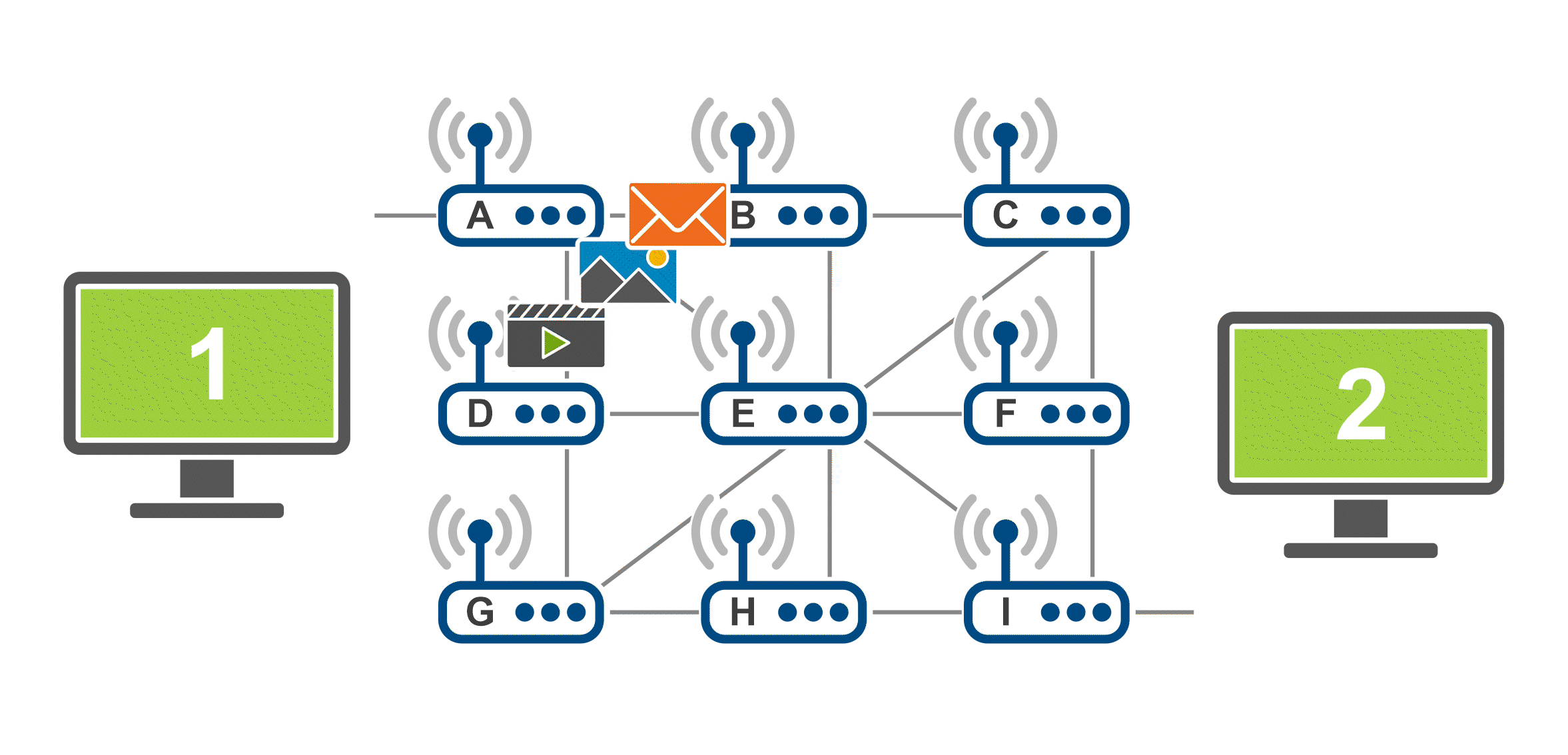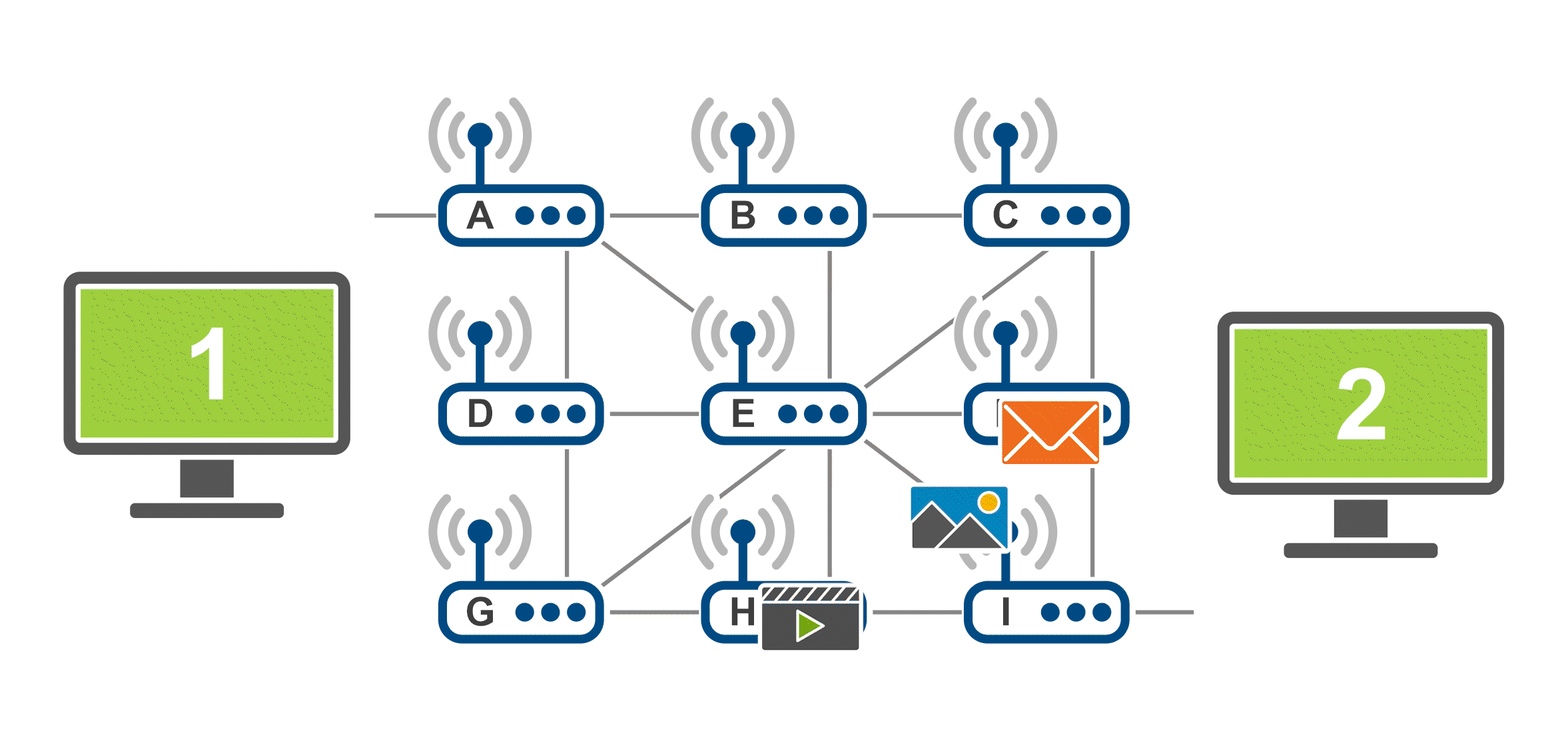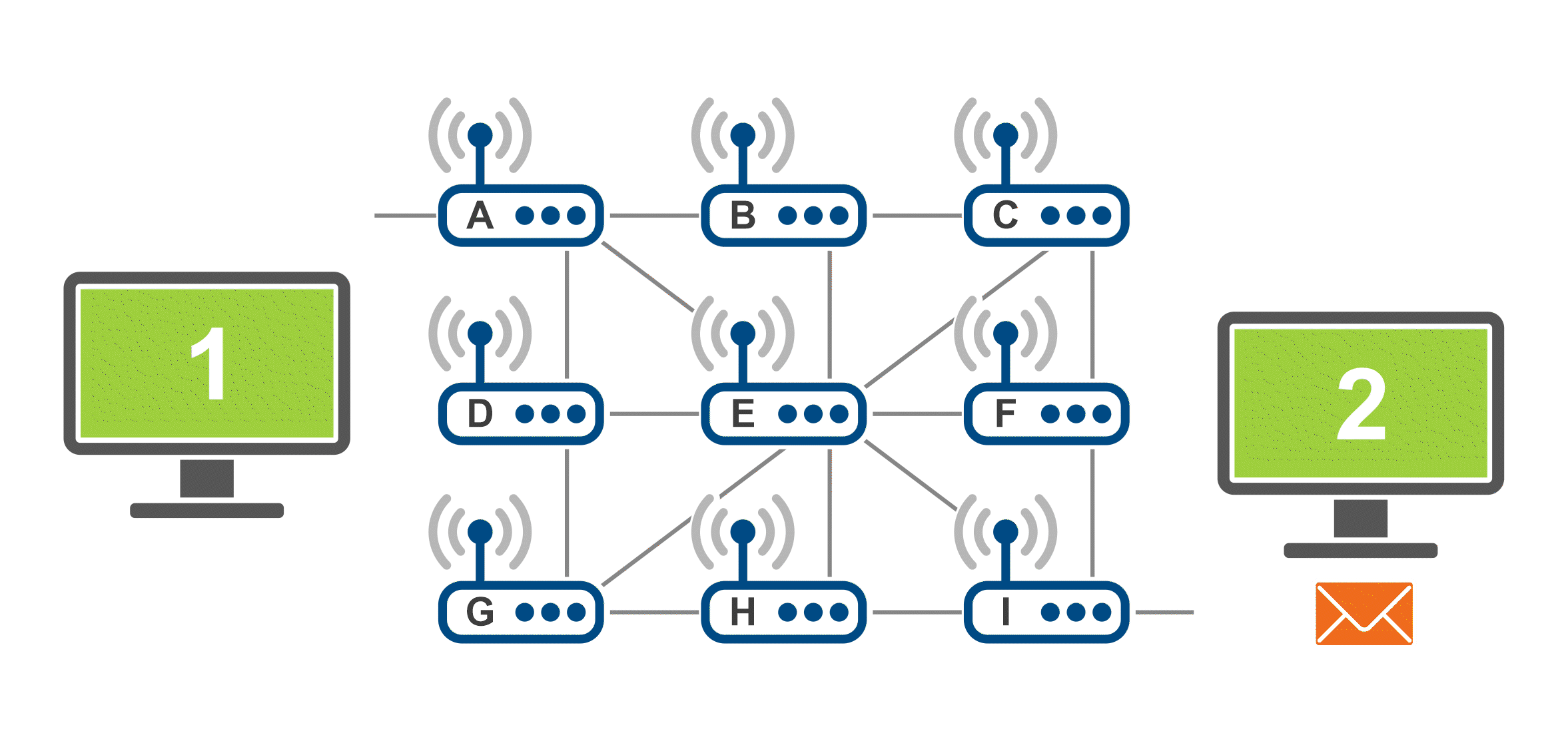
Networking communication protocols
Layer 4
The transport layer is responsible for delivering application data from one node to another. It includes reliable data transfer services to the upper layers in the OSI model and perform error checking to ensure quality of service by resending data if it has been corrupted.
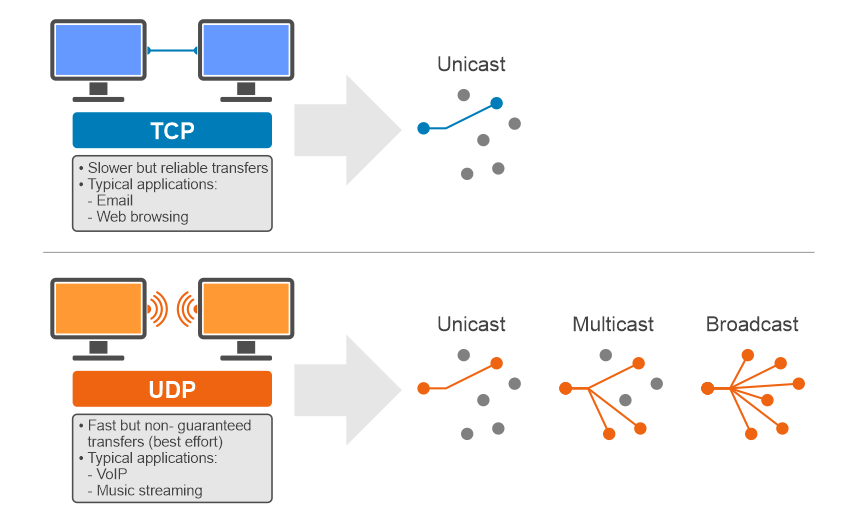
TCP and UDP are the most common protocols used for the transport layer.
Transmission Control Protocol (TCP) provides a reliable delivery of messages over a network. It is a connection-oriented protocol and establishes a connection between the sender and receiver before data can be sent. HTTPS, file transfer, and email use TCP.
User Datagram Protocol (UDP) is a connection-less protocol. It does not establish any connection before sending data and, unlike TCP, it won’t wait for confirmation from other side before sending the next chunk of data. Voice and video streaming use UDP.
A simple illustration: A delivery with a tracking number, carried by a courier, is like TCP. A normal postal delivery without any tracking of its receipt is like UDP.
Layer 5
The session layer is responsible for establishing sessions between the client and server.
Layer 6
The presentation layer is used to interpret and translate messages used by application layer.
Layer 7
The application layer provides an interface for the end-user device connected to the network. This layer deals with the data user view when using these applications, for example, file transfers, printing, web browsing, and emails.
What happens in background when you type www.google.com in your web browser?
- You type www.google.com into address bar of your browser.
- The browser checks the cache for a domain name system (DNS) record to find the IP address of google.com. It checks the following four caches, in order:
- Web browser cache
- OS cache
- Router cache
- ISP cache
- If the requested URL is not found in cache, the ISP DNS server initiates a query, with globally located DNS servers, to find the correct IP address.
- After the browser receives the correct IP address, it initiates a TCP connection with that server.
- The browser sends a HTTP request to the web server and starts communication with the server.
- The web server handles the request from the client and replies with a HTTP response message.
- The web browser displays the HTML content of the www.google.com webpage.
DNS is database that maintains mappings of domain names to IP addresses.
It is used because we humans can remember URLs more easily than complex IP addresses, so DNS helps us to resolve URLs to the exact IP addresses of the web servers where that website is hosted.
Try it!
Question 1: Who is responsible for sending HTTP requests when you try to open a URL?
Question 2: When you open a URL, what is responsible for sending the necessary HTTP requests? The web browser or the web server?
Question 3: A user types this URL www.dell.com in browser’s address bar. Which of the following protocols are used by the browser when fetching and loading the webpage?
IP TCP HTTP HTML IMAP
Related Games